Configure Highly Available VPN with BGP from Azure to GCP
Sep. 10, 2021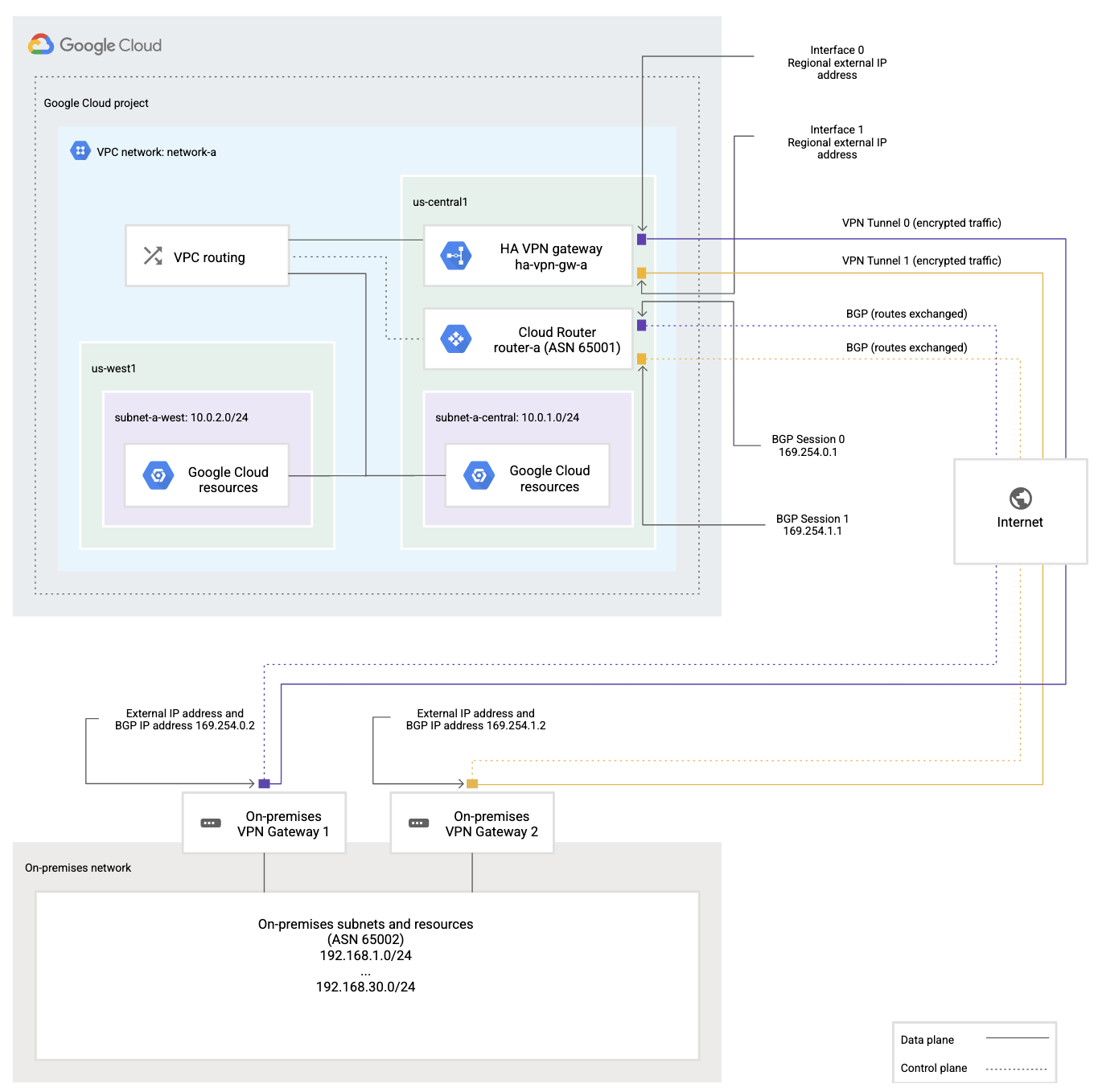
As I am working more and more with multi-cloud customers after creating so called “Landing Zone” the usual next step is to connect on-premises networks and/or another public cloud provider.
In this post I will guide you through creation of Highly Available VPN connection with BGP to dynamically exchange the routes between two cloud providers. I will do it with Microsoft Azure and Google Cloud Platform.
Initial Azure VPN configuration
1.Depends how you want to set it up you can either create a new Resource Group or re-use existing one. In my case I created a new one.

2.In search type gateway and select Virtual Network Gateway. Click Create virtual network gateway.

3.Insert following information:
- Name of the VPN Gateway
- Region
- Gateway Type
- VPN Type
- SKU
- Choose Public IP address
- Create a new one (two if active-active) or re-use existing
- Choose active-active mode
- Configure BGP to exchange the routes
- Enter the BGP ASN
- Provide two BGP network segments

4.Virtual Network - if not created before you can do it in this wizard:
 5.Wait ~30 Minutes to deploy. LOL
5.Wait ~30 Minutes to deploy. LOL
Initial GCP VPN configuration
1.Create a GCP project.

2.Navigate in the menu to Hybrid Connectivity and select VPN.

3.If needed enable missing API’s.

4.Click CREATE VPN CONNECTION.

5.Choose Highly Available (HA) VPN configuration.

6.Provide the VPN Gateway name, network and region.

7.Now we have public IP’s available we can create tunnels. 8.We need to create new peer VPN gateway. Peer VPN gateway is simply Azure VPN Public IP/IP’s.

9.We need to provide a name for our peer VPN gateway and add IP’s. In our case I’ve selected two interfaces.

10.We didn’t create a cloud router in advance we will have to do it in this wizard.

11.We need to enter the router name and Google ASN. I stick to BGP defaults for BGP peer keepalive interval.

12.Now we need to configure two tunnels to the Azure VPN gateway. We need to give it a name and choose or generate IKEv2 pre-shared key

13.Same for the second tunnel.

14.Click create & continue.

15.We are almost at the end of the GCP VPN configuration. Last part is to configure BGP sessions.

16.Configure BGP settings. You will find it in Azure VPN Gateway Configuration section. You must use Azure VPN BGP ASN and previously configured APIPA IP’s.

17.Save the BGP configuration. 18.We also receive a nice overview of the BGP configuration.

Final Azure VPN configuration
So we are pretty much at the very end. We have created all needed resources with configuration in GCP and now we finalize Azure part.
1.In the virtual network gateway go to connections and click add.

2.We need to add and configure tunnels towards GCP VPN. We will use the same pre-shared keys we used in GCP part of configuration.

3.Similar to GCP part we need to add peer network gateways. It is a weird wording from Azure to use local network gateway. Even from Azure point of view local refers to Azure part and not the other side of the tunnel. So we simply add into the local network gateway a public IP of VPN interface 1 from GCP VPN. Weird but works ;)

4.n my case the deployment of local network gateway failed but then it was created. Lol Azure again… It failed because there wasn’t BGP configuration. If it is needed please provide this option during the deployment. Again - fix this please Azure.

5.If you go to local network gateway settings we can now add BGP configuration. We added GCP ASN and configured the GCP cloud router IP address.

6.After configuring the local network gateway with BGP we now are able to configure the tunnel to GCP.

7.Of course configured both tunnels towards GCP.
8.After a few seconds we have connectivity between Azure and GCP.


9.To have final confirmation that tunnels are working in both directions I created two virtual machines in both cloud.


10.SSH works as well. I only needed to allow it on the GCP Firewall side.

Summary
I hope this wizard will be of use to you. In the next post I will create Terraform setup which will be might faster, smoother and easier to follow :)